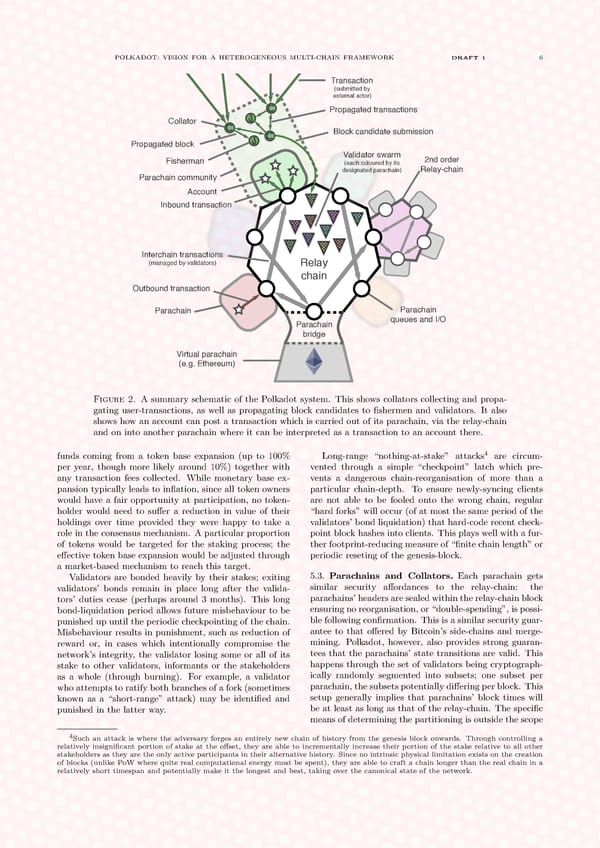
POLKADOT: VISION FOR A HETEROGENEOUS MULTI-CHAIN FRAMEWORK DRAFT 1 6 Transaction (submitted by external actor) Propagated transactions Collator Block candidate submission Propagated block Fisherman Validator swarm 2nd order (each coloured by its Relay-chain Parachain community designated parachain) Account Inbound transaction Interchain transactions (managed by validators) Relay chain Outbound transaction Parachain Parachain Parachain queues and I/O bridge Virtual parachain (e.g. Ethereum) Figure 2. A summary schematic of the Polkadot system. This shows collators collecting and propa- gating user-transactions, as well as propagating block candidates to fishermen and validators. It also shows how an account can post a transaction which is carried out of its parachain, via the relay-chain and on into another parachain where it can be interpreted as a transaction to an account there. 4 funds coming from a token base expansion (up to 100% Long-range “nothing-at-stake” attacks are circum- per year, though more likely around 10%) together with vented through a simple “checkpoint” latch which pre- any transaction fees collected. While monetary base ex- vents a dangerous chain-reorganisation of more than a pansion typically leads to inflation, since all token owners particular chain-depth. To ensure newly-syncing clients would have a fair opportunity at participation, no token- are not able to be fooled onto the wrong chain, regular holder would need to suffer a reduction in value of their “hard forks” will occur (of at most the same period of the holdings over time provided they were happy to take a validators’ bond liquidation) that hard-code recent check- role in the consensus mechanism. A particular proportion point block hashes into clients. This plays well with a fur- of tokens would be targeted for the staking process; the ther footprint-reducing measure of “finite chain length” or effective token base expansion would be adjusted through periodic reseting of the genesis-block. a market-based mechanism to reach this target. Validators are bonded heavily by their stakes; exiting 5.3. Parachains and Collators. Each parachain gets validators’ bonds remain in place long after the valida- similar security affordances to the relay-chain: the tors’ duties cease (perhaps around 3 months). This long parachains’ headers are sealed within the relay-chain block bond-liquidation period allows future misbehaviour to be ensuring no reorganisation, or “double-spending”, is possi- punished up until the periodic checkpointing of the chain. ble following confirmation. This is a similar security guar- Misbehaviour results in punishment, such as reduction of antee to that offered by Bitcoin’s side-chains and merge- reward or, in cases which intentionally compromise the mining. Polkadot, however, also provides strong guaran- network’s integrity, the validator losing some or all of its tees that the parachains’ state transitions are valid. This stake to other validators, informants or the stakeholders happens through the set of validators being cryptograph- as a whole (through burning). For example, a validator ically randomly segmented into subsets; one subset per whoattemptstoratify both branches of a fork (sometimes parachain, the subsets potentially differing per block. This known as a “short-range” attack) may be identified and setup generally implies that parachains’ block times will punished in the latter way. be at least as long as that of the relay-chain. The specific means of determining the partitioning is outside the scope 4 Such an attack is where the adversary forges an entirely new chain of history from the genesis block onwards. Through controlling a relatively insignificant portion of stake at the offset, they are able to incrementally increase their portion of the stake relative to all other stakeholders as they are the only active participants in their alternative history. Since no intrinsic physical limitation exists on the creation of blocks (unlike PoW where quite real computational energy must be spent), they are able to craft a chain longer than the real chain in a relatively short timespan and potentially make it the longest and best, taking over the canonical state of the network.
 POLKADOT Page 6 Page 8
POLKADOT Page 6 Page 8