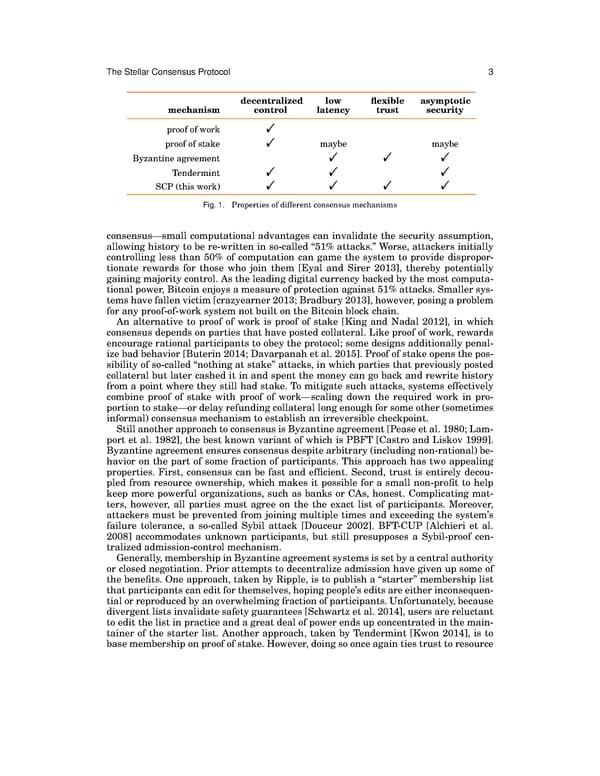
TheStellar Consensus Protocol 3 decentralized low flexible asymptotic mechanism control latency trust security proof of work ✦ proof of stake ✦ maybe maybe Byzantine agreement ✦ ✦ ✦ Tendermint ✦ ✦ ✦ SCP(this work) ✦ ✦ ✦ ✦ Fig. 1. Properties of different consensus mechanisms consensus—small computational advantages can invalidate the security assumption, allowing history to be re-written in so-called “51% attacks.” Worse, attackers initially controlling less than 50% of computation can game the system to provide dispropor- tionate rewards for those who join them [Eyal and Sirer 2013], thereby potentially gaining majority control. As the leading digital currency backed by the most computa- tional power, Bitcoin enjoys a measure of protection against 51% attacks. Smaller sys- temshavefallenvictim[crazyearner2013;Bradbury2013],however,posingaproblem for any proof-of-work system not built on the Bitcoin block chain. An alternative to proof of work is proof of stake [King and Nadal 2012], in which consensus depends on parties that have posted collateral. Like proof of work, rewards encourage rational participants to obey the protocol; some designs additionally penal- ize bad behavior [Buterin 2014; Davarpanah et al. 2015]. Proof of stake opens the pos- sibility of so-called “nothing at stake” attacks, in which parties that previously posted collateral but later cashed it in and spent the money can go back and rewrite history from a point where they still had stake. To mitigate such attacks, systems effectively combine proof of stake with proof of work—scaling down the required work in pro- portion to stake—or delay refunding collateral long enough for some other (sometimes informal) consensus mechanism to establish an irreversible checkpoint. Still another approach to consensus is Byzantine agreement[Peaseetal.1980;Lam- port et al. 1982], the best known variant of which is PBFT [Castro and Liskov 1999]. Byzantineagreementensuresconsensusdespitearbitrary(includingnon-rational)be- havior on the part of some fraction of participants. This approach has two appealing properties. First, consensus can be fast and efficient. Second, trust is entirely decou- pled from resource ownership, which makes it possible for a small non-profit to help keep more powerful organizations, such as banks or CAs, honest. Complicating mat- ters, however, all parties must agree on the the exact list of participants. Moreover, attackers must be prevented from joining multiple times and exceeding the system’s failure tolerance, a so-called Sybil attack [Douceur 2002]. BFT-CUP [Alchieri et al. 2008] accommodates unknown participants, but still presupposes a Sybil-proof cen- tralized admission-control mechanism. Generally,membershipinByzantineagreementsystemsissetbyacentralauthority or closed negotiation. Prior attempts to decentralize admission have given up some of the benefits. One approach, taken by Ripple, is to publish a “starter” membership list thatparticipantscaneditforthemselves,hopingpeople’seditsareeitherinconsequen- tial or reproduced by an overwhelming fraction of participants. Unfortunately, because divergent lists invalidate safety guarantees [Schwartz et al. 2014], users are reluctant to edit the list in practice and a great deal of power ends up concentrated in the main- tainer of the starter list. Another approach, taken by Tendermint [Kwon 2014], is to basemembershiponproofofstake.However,doingsoonceagaintiestrusttoresource
 The Stellar Consensus Protocol Page 3 Page 5
The Stellar Consensus Protocol Page 3 Page 5